Hello and welcome to my academic post! As you might have read in my interactive post(The role of AI in achieving the SDGs in the field of diagnosis and treatment) I mention an artificial intelligence system which can detect retinal disease in medical images. In this post, I raise my concern about the security of medical images when biometric technology has become increasingly popular especially because of the spread of the pandemic virus, Covid-19! Many major medical institutions have nowadays 3D imaging devices, professional remodeling software and 3D printers that can be used to hack biometric identification technology. That’s why I believe that we should be aware of the risk in collecting personal data without hassle and consent.
I hope you find this post informative, and I appreciate you are getting in touch with me by leaving your comments.
Introduction to biometric technology
Biometric technology is used to identify all people by measuring biological characteristics (Dastbaz, 2013). Fingerprint pattern, facial recognition and retina and iris scanning are some of the prominent forms of biometric technology. Researchers claim that each person’s ear shape, how they sit, walk, hand veins, and even facial pimples are unique identifiers. Fig. 1. represents types of biometric authentication (Gillis, 2021).
Fig. 1: Types of biometric authentication.
 ref: TECHTARGET NETWORK
ref: TECHTARGET NETWORK
Some physical characteristics are constant and distinct for each person (even twins), which is why in the last few years they have been used to replace or strengthen password systems. Biometrics is also used in advanced mode to protect sensitive documents. This technology is included in the electronic passports of people around the world with a chip containing a digital photo of the face, fingerprint, or iris scans (Making Travel Faster and Safer – The Promise of Biometric Passports, 2022).
But it is unclear if these extremely accurate biometric technologies are as secure as claimed by their manufacturers. These biometric technologies may deal with serious challenges while three-dimensional (3D) reconstruction based on medical imaging and 3D printing are being developed (Wang & Xue, 2018).
History of biometric technology
The term biometric is derived from the Greek words bio (life) and metric (to measure). In the 2nd century BC, China developed special seals with fingerprints, which were the first step in identification based on individual characteristics (Kindt, 2013). In the 19th century, Alphonse Bertillon (Alphonse Bertillon, 2022), an anthropologist based in Paris, used individual characteristics to identify criminals. Of course, his techniques, although often successful, had no guarantees or reliability (Kindt, 2013). After a while, the use of this technology was completely forgotten. In the following periods, many people started working on this technology again, without knowing how much it would change for future generations.
Since biometric technology provides an acceptable level of confidence in verifying a person’s identity, it significantly improves security. Automatically lock computers and devices by recognizing an approved user’s fingerprint. The door of the server room opens only with the face of trusted managers. These are just some of the applications of this technology. Use of biometric technology consists of several areas including: law enforcement and public security (identification of criminals or suspects), national identification (citizen or voter), military (security matters such as identifying the enemy), border control (identification of travelers or immigrants), commercial applications (consumer or customer identification, and Maintaining security (attendance system in offices or organizations).
Facial recognition technology represents a significant part of the biometric authentication and digital transformation market. Different segments of the facial recognition market, which are quite different from each other, have taken the path of growth and development faster than expected.
The limitations of the two-dimensional face recognition software are not seen in the three-dimensional face recognition software, and this software can work in low light and completely dark environments. The analysis of a facial image may focus on for example the geometric individual features of the face, on skin texture, but also the comparative distance between and directions of specific points in the face (Kindt, 2013). Images are taken by a consumer camera with basic functionality may also be suitable for analysis (Fig. 2).
Fig. 2: the image which may also be suitable for face recognition analysis.
 ref: Els J. Kindt
ref: Els J. Kindt
“Facial image taken of visitor for access control purposes and issuance of badge at the European parliament (© E. Kindt. When the facial image was taken, which was mandatory for entering the building as visitor, a specific position was to be adopted. No information was provided to the data subject about the use and purposes of the collection of the facial image, the controller of the processing and access rights).”
Simultaneously with the increase of investments in the field of facial recognition technologies as well as the maturity and evolution of technologies, the amount of use of this technology in some cases, including new cases of use, increases. One of the main reasons for the increase in the use of facial recognition technology is the spread of the corona virus.
In addition, the outbreak of the Covid-19 virus has led to the development of facial recognition systems that are equipped with other biometric authentication techniques. As a result of the spread of the corona virus, digitization is expected to accelerate in some areas. So far, plenty of work has been done in the field of masked face recognition. A masked face dataset has been created by Wang et al which is available for free for industry and academia. (Qayyum, 2020).
The growth and expansion of the facial recognition market because of the spread of the pandemic virus, Covid-19
As a result of the spread of the Covid-19 pandemic virus, facial recognition technologies are increasingly used in the field of digital health and treatment; Facial recognition technology is combined with other biometric authentication techniques, and some applications are equipped with it, and these applications are used to detect people who are wearing face shields or in fever measurement, thereby preventing the spread of disease.
It is no secret that the needs caused by the spread of the corona virus origin changes in the dynamics of the facial recognition market. According to ABI Research report release, the value proposition of algorithm developers currently includes face and iris recognition technologies that allow authentication and detection (and inevitably surveillance) of people who are fully or partially covered.
In addition, technologies that enable fever or temperature measurement, which are used in many countries, have been updated in access and border control (Facial Recognition Technology Market Driven By The COVID-19 Pandemic, 2022).
Biometric technology, good or bad?
There is an important reason for the increasing popularity of biometric technology because most believe that it is difficult to fake. Identity verification is done with unique features, so many think that the possibility of fraud will be very low and hence it greatly increases the security of organizations.
Keeping secure has started with passwords and passwords can be forgotten or leaked. People who know you guess your password and hackers figure it out by playing the numbers game. It seems very difficult to forge and confirm with individual characteristics. But it might be wrong!
In fact, breaking many biometric systems is easy if some of the medical imaging materials commonly used by doctors are available.
Three-dimensional (3D) reconstruction of the face at different levels of detail can be done through several methods, including magnetic resonance imaging (MRI), traditional computed tomography (CT), and 3D medical scanner. What if by using these methods facial reconstructions can be 3D printed and utilized to break and hack facial recognition devices?
Assumption
Is biometric technology threatened by the development of medical imaging?
A medical 3D scanner subsequently printed on a 3D printer with high precision can provide an accurate reconstruction of the human face. Existing facial recognition technologies are at risk if some changes are done to the 3D models. This is mainly true for some low security facial recognition systems, that can be simply attacked by regular medical imaging data (MRI or CT head scanning data). Fig. 2. shows the result of CT-based facial 3D reconstruction.
Fig. 2: Some CT-based facial 3D reconstruction images.
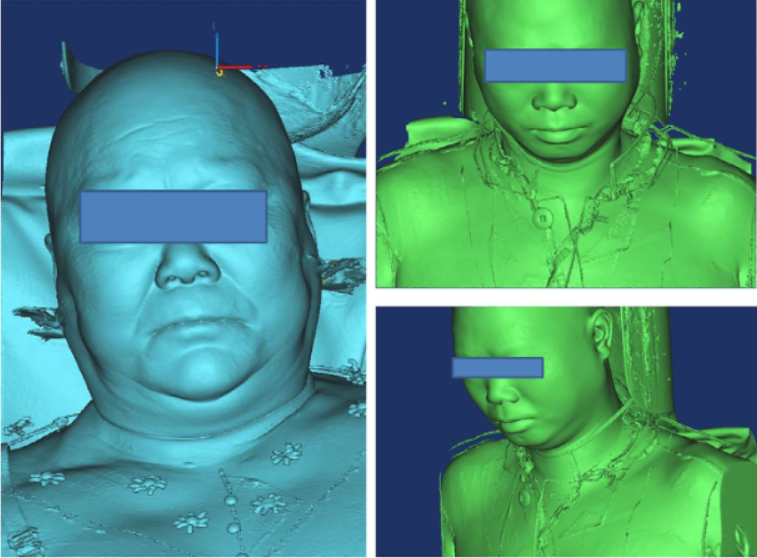 ref: Medical Hypotheses
ref: Medical Hypotheses
As many medical fields have become digitalized, there are a lot of imaging data which are saved digitally. These types of imaging can be used for three-dimensional reconstruction. But if the IT systems where these medical data are stored,in-cloud medical data storage servers, are leaked or hacked, there will be huge security problems.
Discussion
The risk of facial recognition systems being hacked is increasing and it has been reported that 3D printing has been used to hack facial recognition systems. This risk is increasing due to the rapid digitalization of medical big data. It has been heavily invested in the use of artificial intelligence in the medical imaging. Medical imaging data in both the training phase and the application phase by artificial intelligence. But what are the possible channels for disclosing this medical big data? As mentioned earlier, it is possible for someone to hack into cloud medical data storage servers. Also, some doctors are not aware of the importance of confidentiality of patient’s information and unfortunately may share some data unintentionally. I similarly note that in some countries due to the lack of sufficient privacy laws, medical big data are easily accessible. Privacy advocates fear violations of related laws by some closed artificial intelligence companies which may resell their medical big data.
It is time to pay attention to biometric security. Assume that our password is hacked and exposed, we can easily change the password. But what should we do if our biological information, which was supposed to be secure in the medical bid data, is hacked?
To deal with such incidents, we need a multifaceted strategy. Medical institutions should be careful in collaborating with artificial intelligence companies and should stablish a proper data management system. Physicians should be aware of patient privacy regulations after obtaining medical information.
One thing that is clear, every change has always had many supporters and opponents. Neither the opponents have been able to prove its negative points with certainty, nor have the supporters been satisfied with them. But the efficiency of devices equipped with biometric technology has led to a positive change over time and it just needs to be protected from being hacked.
Reflection
I worked in a med-tech company with the focus of an artificial intelligence medical service software for healthcare professionals and patients. I always had an interest in knowing more about how artificial intelligence and big data promote disease prevention, enable remote consultations, automate translation and documentation, and provide diagnosis and treatment support. New Media, Information Communication Technology (ICT), and Development course has given me the opportunity to investigate this topic for development purposes. My investigation has been started by exploring the potential applications of AI in the field of medicine. Then, in my interactive post I write about how medical imagery big data is combating diabetes blindness. Finally, in my interactive post, I raise my concern about the security of medical images.
Some of the literature that I have encountered while doing this assignment helped me understand the vast amount of data that is distributed around the world, for better or for worse. People are so busy collecting data that they ignore the fact that data which is rarely used is misused.
By reading the other students posts, I have learned that new media and ICT are effective ways of communication, and they are approaches for social change and development.
From the technical side, the platform where we publish our posts is WordPress. From its easy-to-use dashboard to its customization options, WordPress is user friendly, but some basic front-end programming skills might be needed to get the exact look.
The intention of our group is to make people think more about impacts on the use of big data but also on the benefits when it is used in an ethical manner. The group try to communicate through University Canvas and WhatsApp to respect deadlines. Each group member has individual role which helps the team to work more agile.
References
Alphonse Bertillon. (2022, 11 4). Retrieved from Wikipedia: https://en.wikipedia.org/wiki/Alphonse_Bertillon
Dastbaz, M. (2013). Emerging Technologies and the Human Rights Challenge of Rapidly Expanding State Surveillance Capacities. In A. B, Strategic Intelligence Management (pp. 108-118). eLSEVIER SCIENCE.
Facial Recognition Technology Market Driven By The COVID-19 Pandemic. (2022, 1107). Retrieved from Airpix: https://airpix.io/facial-recognition-covid19-blog.html
Gillis, A. (2021, 07). biometrics. Retrieved from TechTarget: https://www.techtarget.com/searchsecurity/definition/biometrics
Kindt, E. (2013). An Introduction into the Use of Biometric Technology. Privacy and Data Protection Issues of Biometric Applications , 15-85.
Making Travel Faster and Safer – The Promise of Biometric Passports. (2022, 07 21). Retrieved from Aware: https://www.aware.com/blog-faster-safer-travel-biometric-passports/
Qayyum, I. (2020). Towards Facial Recognition Problem in COVID-19 Pandemic. 2020 4rd International Conference on Electrical, Telecommunication and Computer Engineering (ELTICOM), 210-214.
Wang, Y., & Xue, C. (2018). Medical information security in the era of artificial intelligence. Medical Hypotheses, 58-60.


