Reading time: 4 minutes, 12 seconds.
For this week’s blog post, I am presenting the highlights of James Obuhuma’s presentation of his report on “Social engineering-based cyber attacks in Kenya” during the IST-Africa 2020 Conference Proceedings, Session 20. This report is written by James Obuhuma and Shingai Zivuku, and its main objective is to introduce an analytical approach towards social engineering in Kenya and to develop a model for controlling and minimizing cyber attacks.
Cybersecurity is a compelling challenge in the period of the fourth Industrial Revolution and the Internet of Things (IoT) booms. While cybercriminal activities are perceived as complex happenings, organizations invest in technology to protect from cybercriminal strategies and create defense-in-depth strategies. Yet, social engineering is one of the greatest threats to information systems (IS) since social engineering results in psychological attacks and exploits the weakest layer of IS: people. To explore the level of understanding of the diverse forms of social engineering of Kenyans, Obuhuma and Zivuku collected information through an online survey and face to face interviews.
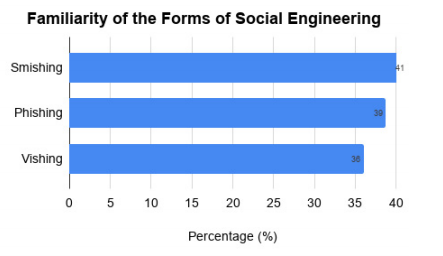
The study shows that Kenyans did not know for certain what social engineering was unless it was explained to them. However, they were mostly familiar with the terms smishing (41%), them phishing (39%), and lastly vishing (36%), as shown in Figure 1. To clarify, phishing is a form of financial fraud that misleads people by email. Smishing is when criminals send text messages (SMS) to encourage people to pay on suspicious links, while vishing includes a fraudulent phone call where criminals attempt to persuade people to provide information needed for financial gain.
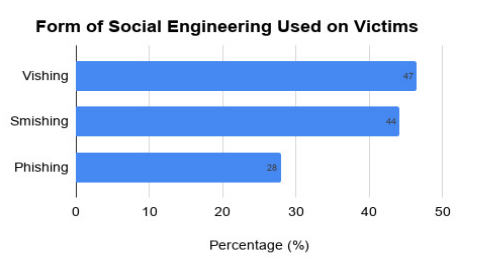
While social engineering attacks were mainly vishing (47%) and smishing (44%) in Kenya, phishing was slightly less (with a score of 28%) compared to the other forms as evident in Figure 2. Vishing and smishing is much more prevalent because of the growth in mobile phone usage and mobile money transfers, unprotected personal data by mobile money transfer agents. Furthermore, these forms of attacks are also applicable to feature phones. As personal data is collected by money transfer agents, this enables attackers to gain more information about target victims. Smishing is also a cheaper form of cyber-attack because of its low cost of SMS. Despite the fact that vishing and smishing are relatively more common compared to phishing, phishing involves writing long convincing messages with clickable links to phishing sites. This factor gives it the upper hand rather than vishing and smishing. In addition to this, the study identifies the motives behind the cyber-attacks as financial gain and identity theft with the aim of getting financial gain.
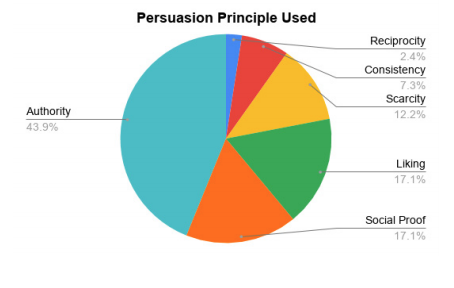
As shown in Figure 3, there are six general persuasion skills that are used by cyber-attackers to make people not realize that they are being attacked: authority, social proof, liking, scarcity, consistency and reciprocity (Bullee et al., 2018). Authority is used the most compared to other persuasion skills. Authority, in this context, refers to the idea that attackers put themselves in an authority position to let people think that information is requested from a higher position.
More than half of Kenya’s population feels as if there are no laws on social engineering. While a few people stated that there are laws on social engineering, they could not quote any of the laws. While suggested solutions for these cyber attacks involve user education, enactment of laws, enforcement of laws, strict penalties including blacklisting, innovative solutions (AI Prediction Systems), regulation and tough laws for telcos, special police unit, formulation of policy, resolution facilitation for law enforcers, prompt incidence response, better data and network administration, IP address tracking, and media surveillance, Obuhuma demonstrates that increasing user education and awareness is the core solution. Enhanced knowledge and awareness of users can help to identify the persuasion skills and hinder the risk of being a victim of cyber attacks.
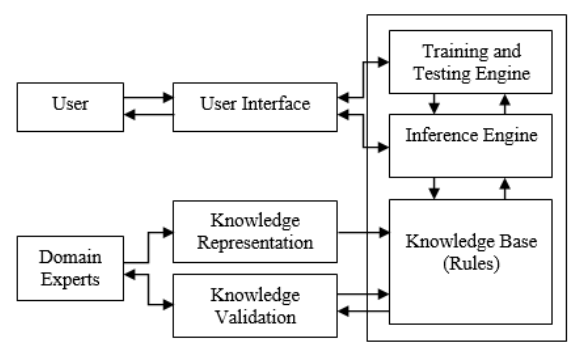
As shown in Figure 4, the Social Engineering Model encompasses key phases such as knowledge acquisition, knowledge representation, knowledge validation, inferencing and explanation, and justification. Acquisition and validation of knowledge requires domain experts to disclose knowledge and turn it into rules and guidelines for people to use. In this way, specific rules and guidelines will enable the inference engine to correlate users’ actions against the persuasion principles. ‘Training and testing engine’ aids to test and link to the knowledge while ‘user interface’ is a chatbot that could be a web application or mobile app that provides efficient interaction for users. This model helps to create awareness for the users and it helps them to provide a capability to identify the persuasion principles.
As many Kenyans become victims of Social Engineering attacks because of their lack of awareness and/or user education, Obuhuma and Zivuku’s study shows that there should be an awareness model to generate a society with more knowledge of cyber-attacks and reduce the rate of successful attacks. As the weakest link to IS is people, this model can be beneficial for individuals and organizations at the same time.
Do you think that this model would be efficient?
We would love to hear your thoughts on this study!
Download the full report here.
The presentation is also available for users on Youtube.
This post is written by Aylin Karaarslan. Find out more about the authors of this blog.
References
Bullée, J.W.H., Montoya, L., Pieters, W., Junger, M., & Hartel, P. (2018, January). On the
anatomy of social engineering attacks—A literature-based dissection of successful
attacks. Journal of Investigative Psychology and Offender Profiling, 15 (1): 20–45.
45. https://doi.org/10.1002/jip.1482
Obuhuma, J., & Zivuku, S. (2020, May 20). Social Engineering Based Cyber-Attacks in Kenya
[Paper presentation]. In Cunningham, M., & Cunningham, P. (Eds). IST-Africa 2020
Conference Proceedings. IST-Africa Institute and IIMC, Session 20, ISBN: 978-1-905824-
64-9.

